What does service mesh have to do with security
The problem
- Kubernetes is not secure by default
- How to manage certificates and identity ?
- How to do the above without too much work in the developer side ?
- How to limit lateral movement inside kubernetes ?
Network policy to manage identity ?
- Not a real identity
- In cloud native world, could have problems with dinamic ip association
Introducing the sidecar Model
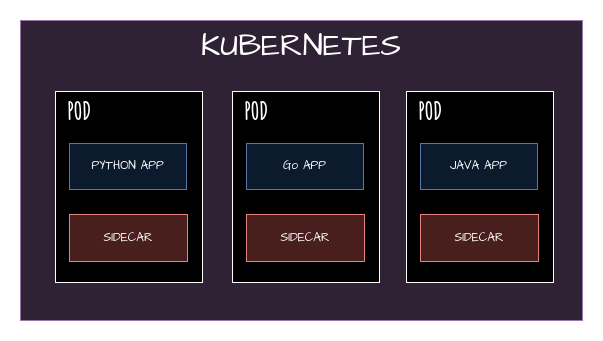
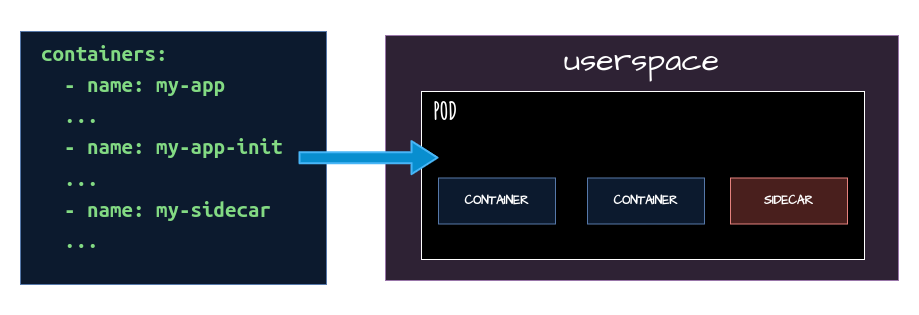
The sidecar Model has yaml
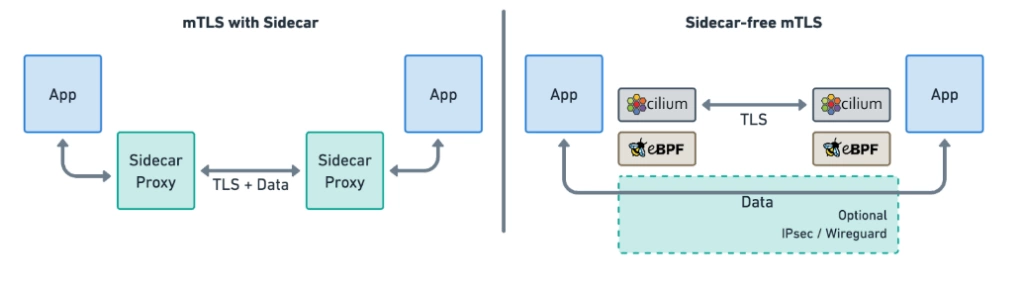
The sidecarless Model
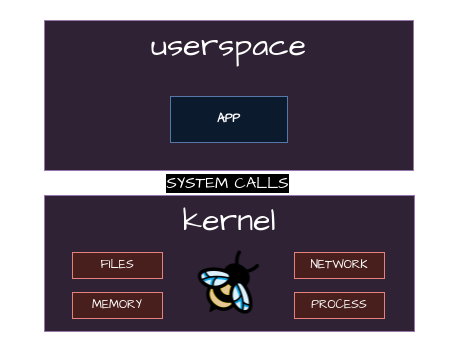
What is eBPF ?
extended Berkley Packet Filter
Look Ma’s, without sidecar
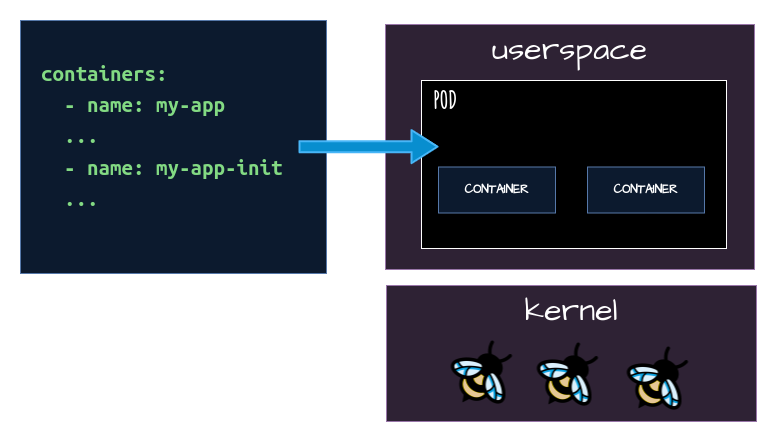
Sidecar vs eBPF
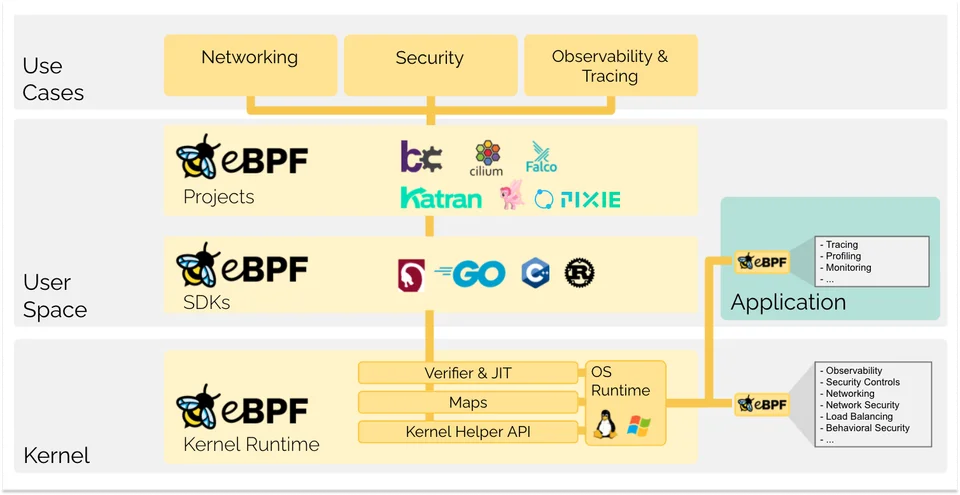
eBPF Architecture
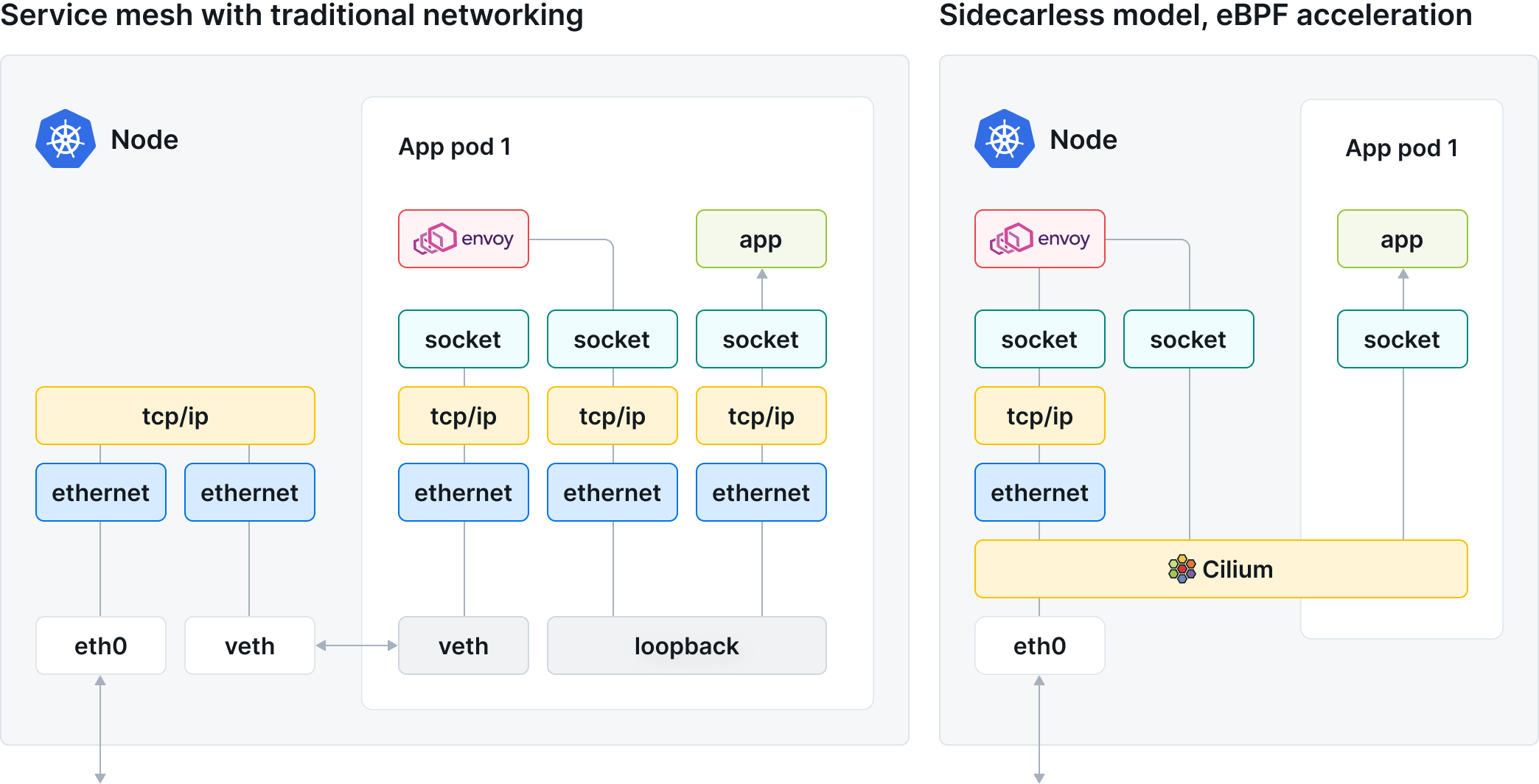
Cilium eBPF with envoy ?
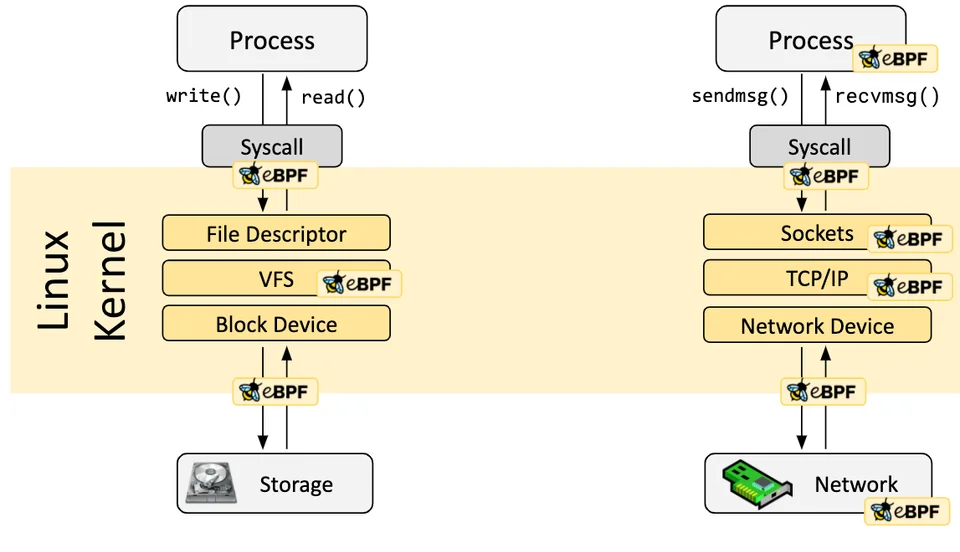
eBPF Hook Overview
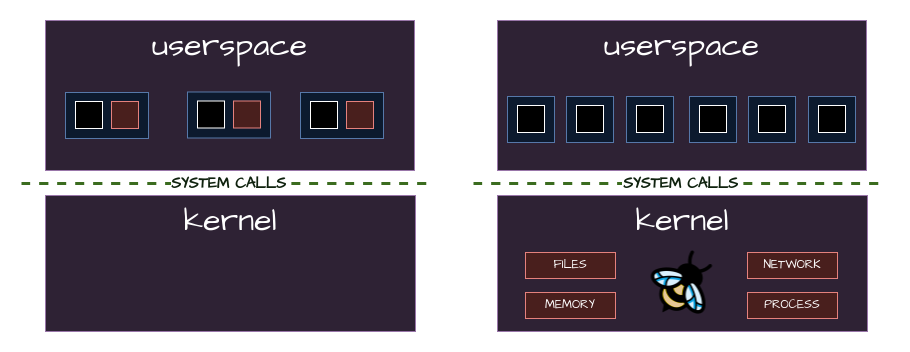
Security with ebpf
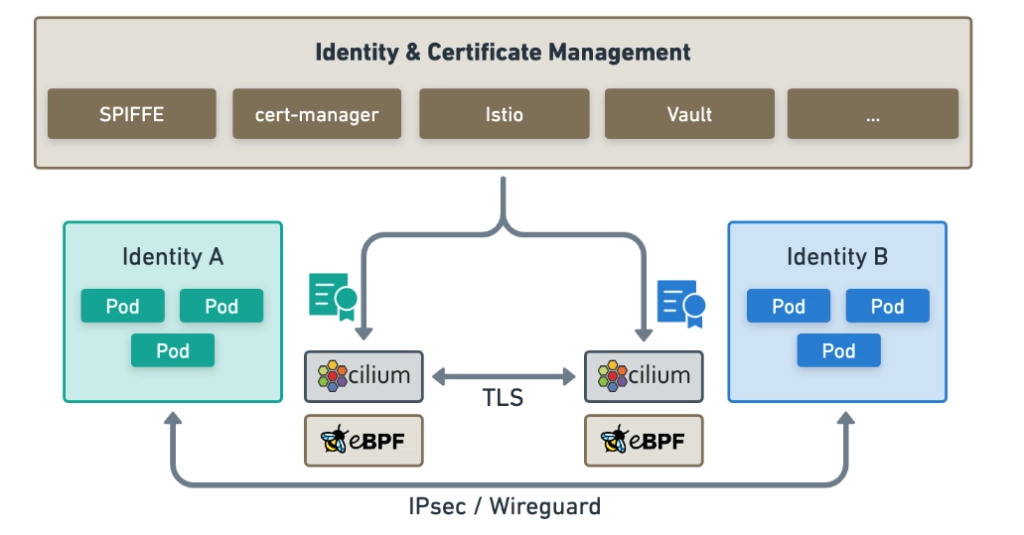
But what about Service Mesh ?
Traffic Management
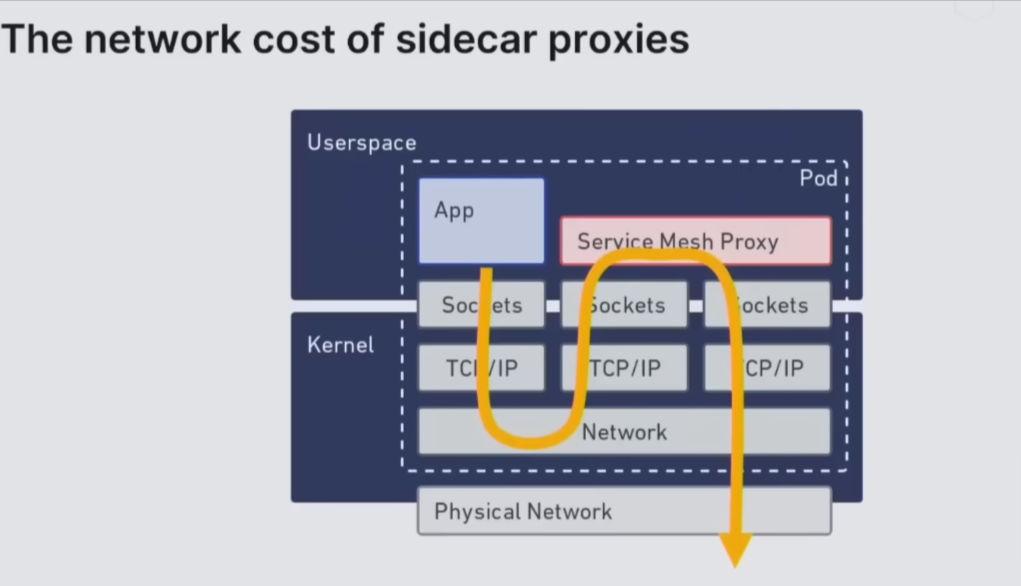
The network cost of sidecar proxies
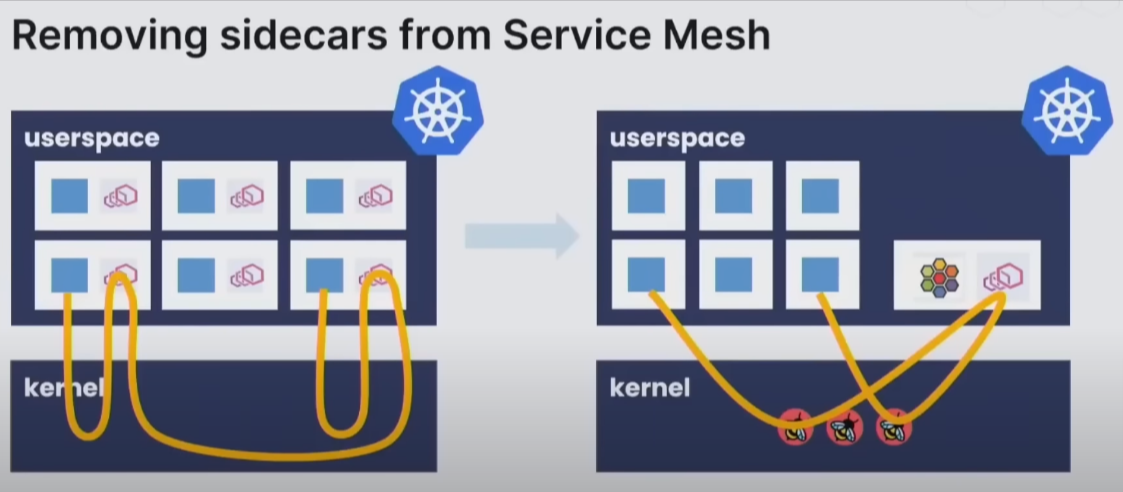
Without sidecars
Removing sidecars from Service Mesh
Evolution ? Not exactly, yet
Can We move Service Mesh to the Kernel ? Kinda off…
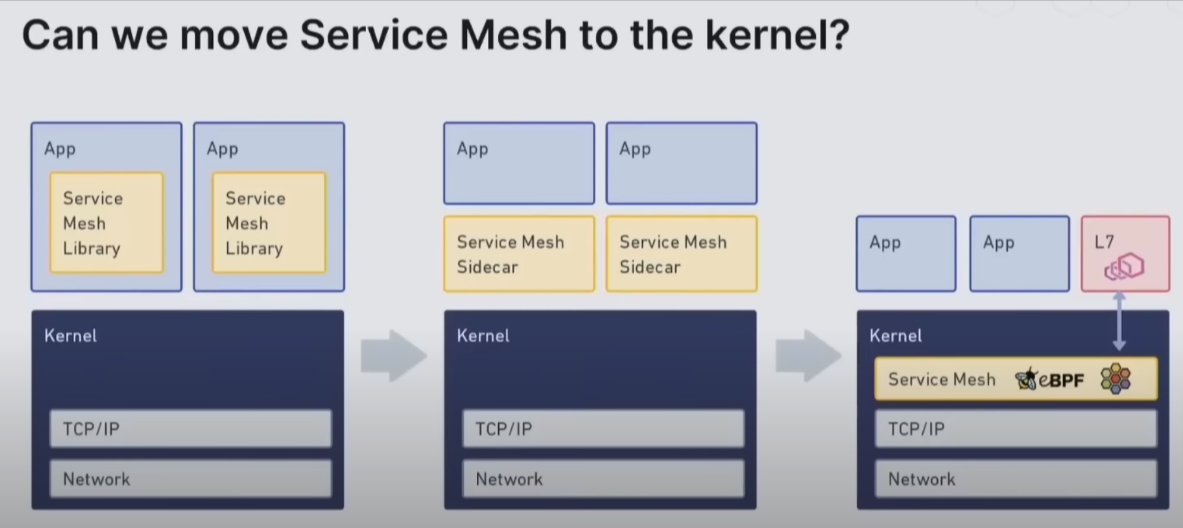
Tradeoffs
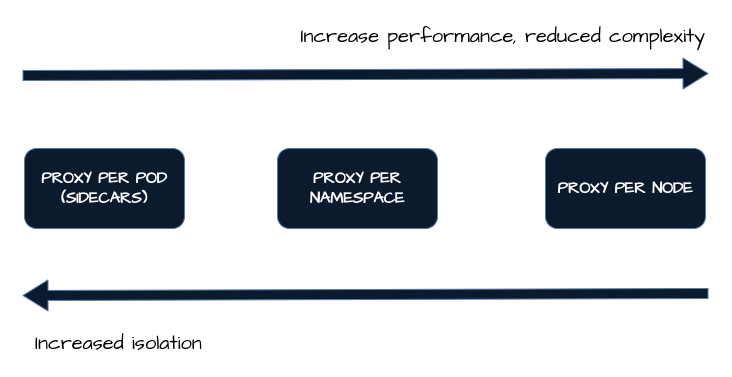
What about Istio ?
Security Overview
Istio Security
The Istio security features provide strong identity, powerful policy, transparent TLS encryption, and authentication, authorization and audit (AAA) tools to protect your services and data.
Goals of Istio security
- Security by default: no changes needed to application code and infrastructure
- Defense in depth: integrate with existing security systems to provide multiple layers of defense
- Zero-trust network: build security solutions on distrusted networks
Istio Architecture
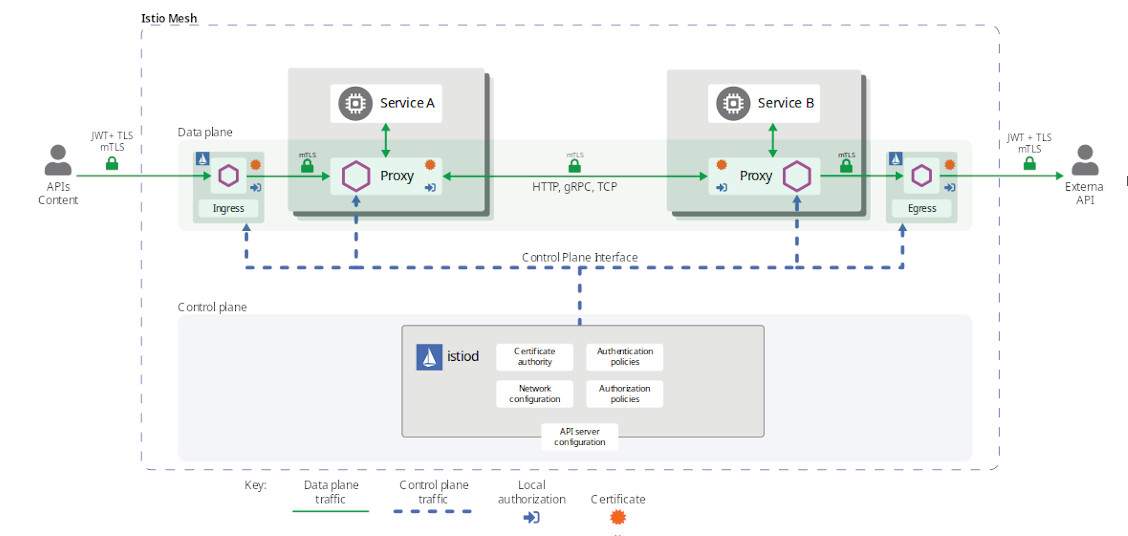
Identity And Certificate Management
Identity Provisioning Workflow
Authentication Architecture
Policy
PeerAuthentication
Authorization Architecture
Policy
AuthorizationPolicy
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: httpbin
namespace: foo
spec:
action: ALLOW
rules:
- from:
- source:
principals: ["cluster.local/ns/default/sa/sleep"]
- source:
namespaces: ["test"]
to:
- operation:
methods: ["GET"]
paths: ["/info*"]
- operation:
methods: ["POST"]
paths: ["/data"]
when:
- key: request.auth.claims[iss]
values: ["https://accounts.google.com"]Routes with VirtualService
Public routes & Private Routes
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: reviews-route
spec:
hosts:
- reviews.prod.svc.cluster.local
http:
- name: "reviews-v2-routes"
match:
- uri:
prefix: "/wpcatalog"
- uri:
prefix: "/consumercatalog"
rewrite:
uri: "/newcatalog"
route:
- destination:
host: reviews.prod.svc.cluster.local
subset: v2
- name: "reviews-v1-route"
route:
- destination:
host: reviews.prod.svc.cluster.local
subset: v1Cors
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: ratings-route
spec:
hosts:
- ratings.prod.svc.cluster.local
http:
- route:
- destination:
host: ratings.prod.svc.cluster.local
subset: v1
corsPolicy:
allowOrigins:
- exact: https://example.com
allowMethods:
- POST
- GET
allowCredentials: false
allowHeaders:
- X-Foo-Bar
maxAge: "24h"Extending functionality with WASM
WasmPlugins provides a mechanism to extend the functionality provided by the Istio proxy through WebAssembly filters.
apiVersion: extensions.istio.io/v1alpha1
kind: WasmPlugin
metadata:
name: openid-connect
namespace: istio-ingress
spec:
selector:
matchLabels:
istio: ingressgateway
url: file:///opt/filters/openid.wasm
sha256: 1ef0c9a92b0420cf25f7fe5d481b231464bc88f486ca3b9c83ed5cc21d2f6210
phase: AUTHN
pluginConfig:
openid_server: authn
openid_realm: ingress
SPIFFE, the Secure Production Identity Framework For Everyone, provides a secure identity, in the form of a specially crafted X.509 certificate, to every workload in a modern production environment.
SPIFFE removes the need for application-level authentication and complex network-level ACL configuration.
What is SPIRE?
SPIRE, the SPIFFE Runtime Environment, is an extensible system that implements the principles embodied in the SPIFFE standards. SPIRE manages platform and workload attestation, provides an API for controlling attestation policies, and coordinates certificate issuance and rotation.
All powered by MTLS
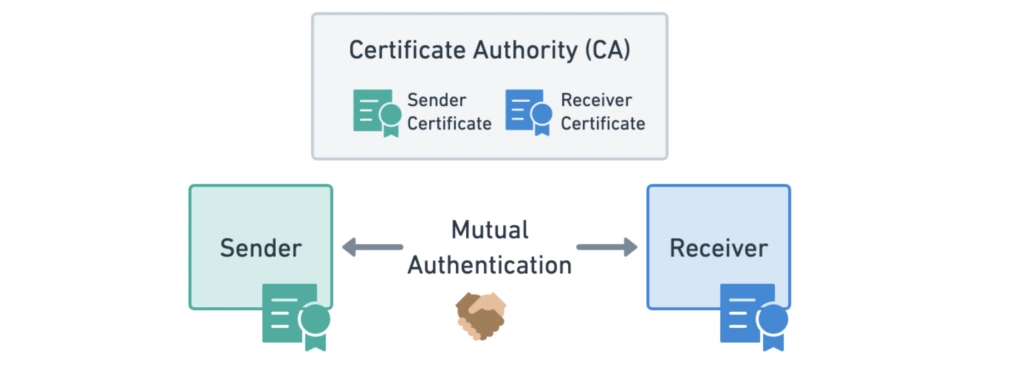
Session VS Network based authentication
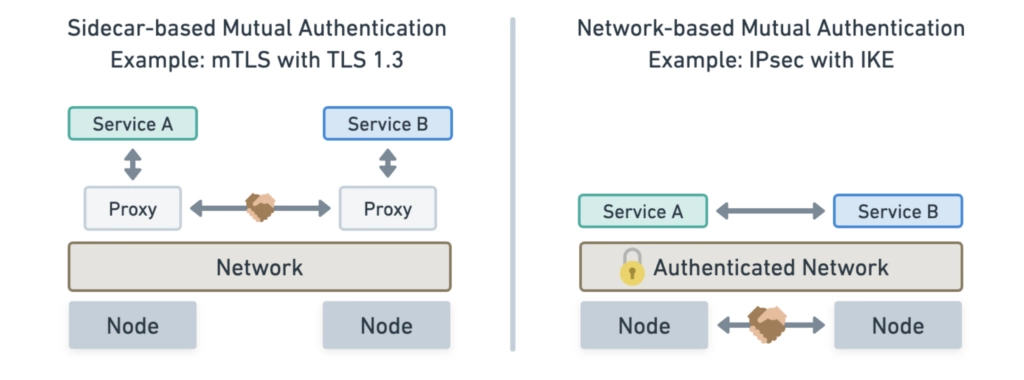
With Sidecar VS Sidecarless
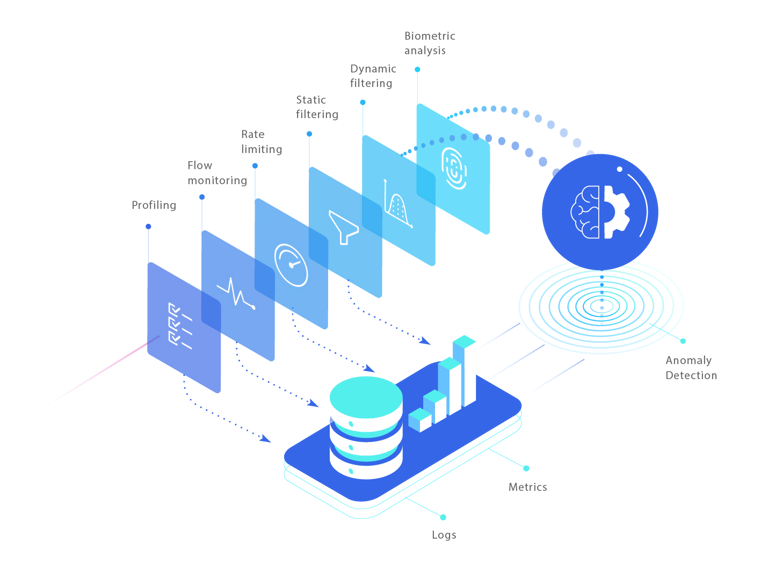
Envoy with curiefense
Curiefense is an API-first, DevOps oriented web-defense HTTP-Filter adapter for Envoy and NGINX. It provides multiple security technologies (WAF, application-layer DDoS protection, bot management, and more) along with real-time traffic monitoring and transparency.
Curiefense architecture
Demo Time
- Show diagrams (next slide)
- Show code
- Show console commands
- Show kiali, grafana and jaeger
- Show istio documentation
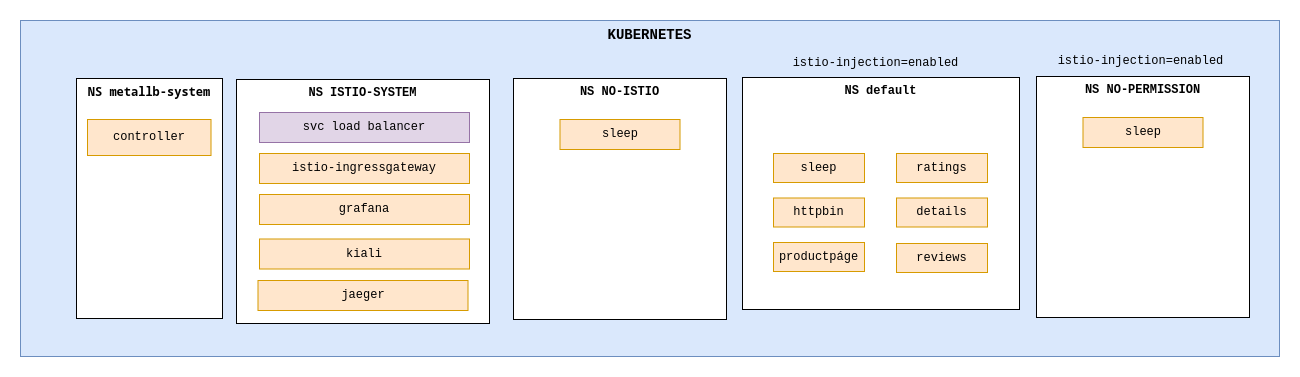
Kubernetes Part
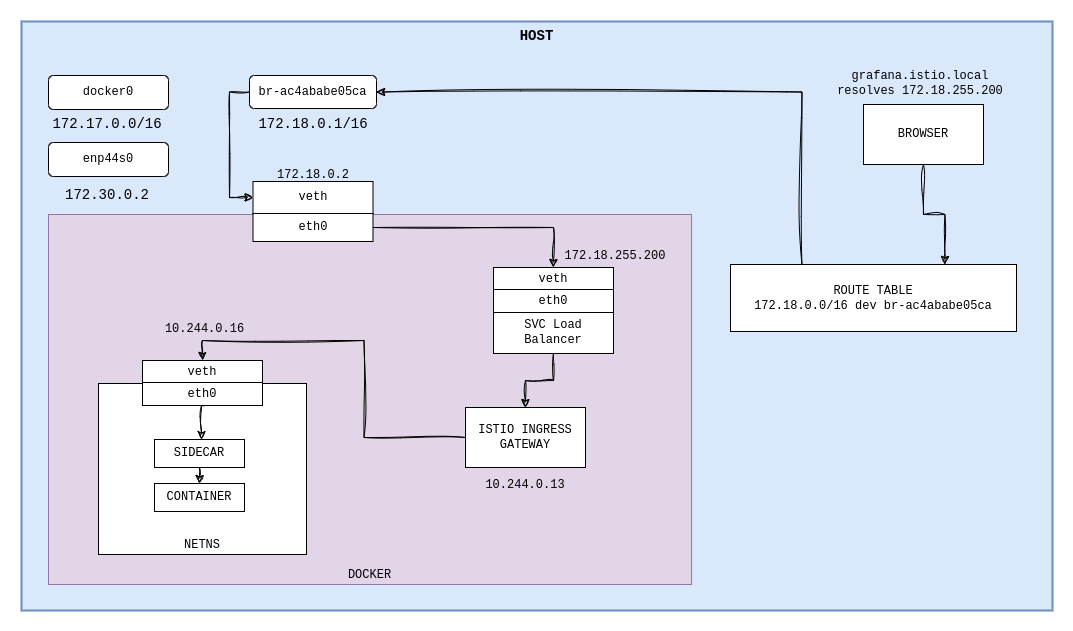
Network Part
References
- https://istio.io/latest/docs/concepts/security
Questions ?
Istio is awesome